The hardest problems to diagnose are those involving multiple products. We received a call from one of our managed customers, he had an existing PC when we onboarded them. His initial call claimed that ThreatLocker had blocked his Excel program. That seemed unlikely, so I glanced at the audit log and didn’t see anything and jumped into a remote session and called the customer.
When opening a xlsx file or opening Excel directly, we got this error:
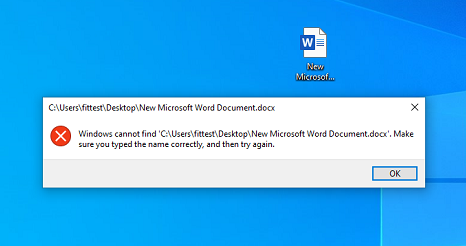
In ThreatLocker, when we clicked on a xlsx or docx file, ThreatLocker Realtime Action Log showed that a CCleaner executable was activating. We don’t use CCleaner, it was a remnant of the previous MSP, so I uninstalled it but still the software would not load. I tried quick fix on Office 2019 and online fix, no change.
I talked with another senior tech and we both agreed, this seems familiar but couldn’t remember what phrases to search on to locate the solution.
It specifically targeted only these Office executables though. I started to get desperate so I broke out Process Monitor and started examining it from the start of the winword.exe call. As I scrolled I noticed an old familiar phrase, see if you can “Where’s Waldo” it:
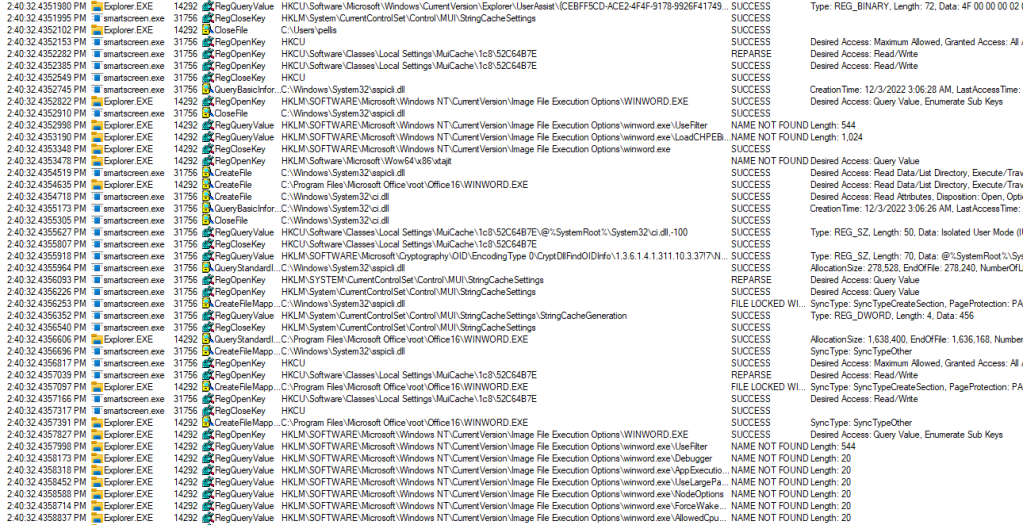
So the reason we remembered this is because it’s a common malware tactic from ages ago, IFEO

Image File Execution Options was the culprit. This allows you to attach a debugging process to any other executable, malware would attach to things like explorer.exe making it nearly impossible to clean up especially if it also had a guardian exe keeping it persistent.
I examined the registry and sure enough, found multiple entries with a debugger that was a CCleaner process that no longer existed:
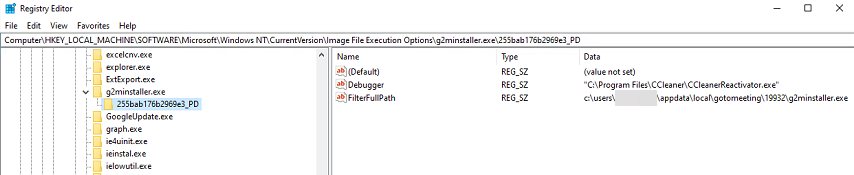
Commonly AV or some other malware tool would find the malicious process and remove the process but wouldn’t find that it was attached here, so we would have to locate it and remove it manually. I don’t see those issues any more since we’re using better security tools and I think it might have fallen out of favor with malware.
Once those errant entries were removed the software loaded normally, we also found other applications that were blocked too so we fixed those as well.
So the root cause analysis was that CCleaner auto-updated, since the update exe was in TL policy list, it allowed it to run and write new executables, but those new executables are not in any of the policies so they were blocked by TL. CCleaner is not really on our list of good apps so it was best practice to remove these types of programs as they tend to break things, case in point. The uninstall process for some reason did not reverse these IFEO entries and then we couldn’t launch any of the programs CCleaner attached to, mainly Office products. Removing the entries returned the programs to a debugger free operation mode again.